SSL encryption
Memgraph uses SSL (Secure Sockets Layer) protocol for establishing an authenticated and encrypted connection to a database instance.
Achieving a secure connection is a three-step process that requires
- Owning a SSL certificate
- Configuring the server
- Enabling SSL connection
For any errors that might come up, check out the Help center page on errors.
SSL certificate
SSL certificate is a pair of .pem documents issued by self-signing, or by a
Certification Authority. Memgraph contains a self-signed testing certificate
(cert.pem and key.pem) located at /etc/memgraph/ssl/.
If you are using Docker and want to use your own certificates, you need to move them into a Docker container in order to utilize them.
Configure the server
To use a certain SSL certificate, change the configuration file to include the
--bolt-cert-file and --bolt-key-file flags and set them to the location of
the certification files.
If you are using the Memgraph self-signed certificate, set the configuration flags to:
--bolt-cert-file=/etc/memgraph/ssl/cert.pem
--bolt-key-file=/etc/memgraph/ssl/key.pem
When using Linux, be sure that the user memgraph has permissions (400) to
access the files.
Once the flags are included in the configuration, you cannot establish an insecure connection.
Enable SSL connection
- Memgraph Lab
- mgconsole
- Drivers
- WebSocket
To enable SSL connection in Memgraph Lab, switch to Connect Manually view and turn the SSL on.
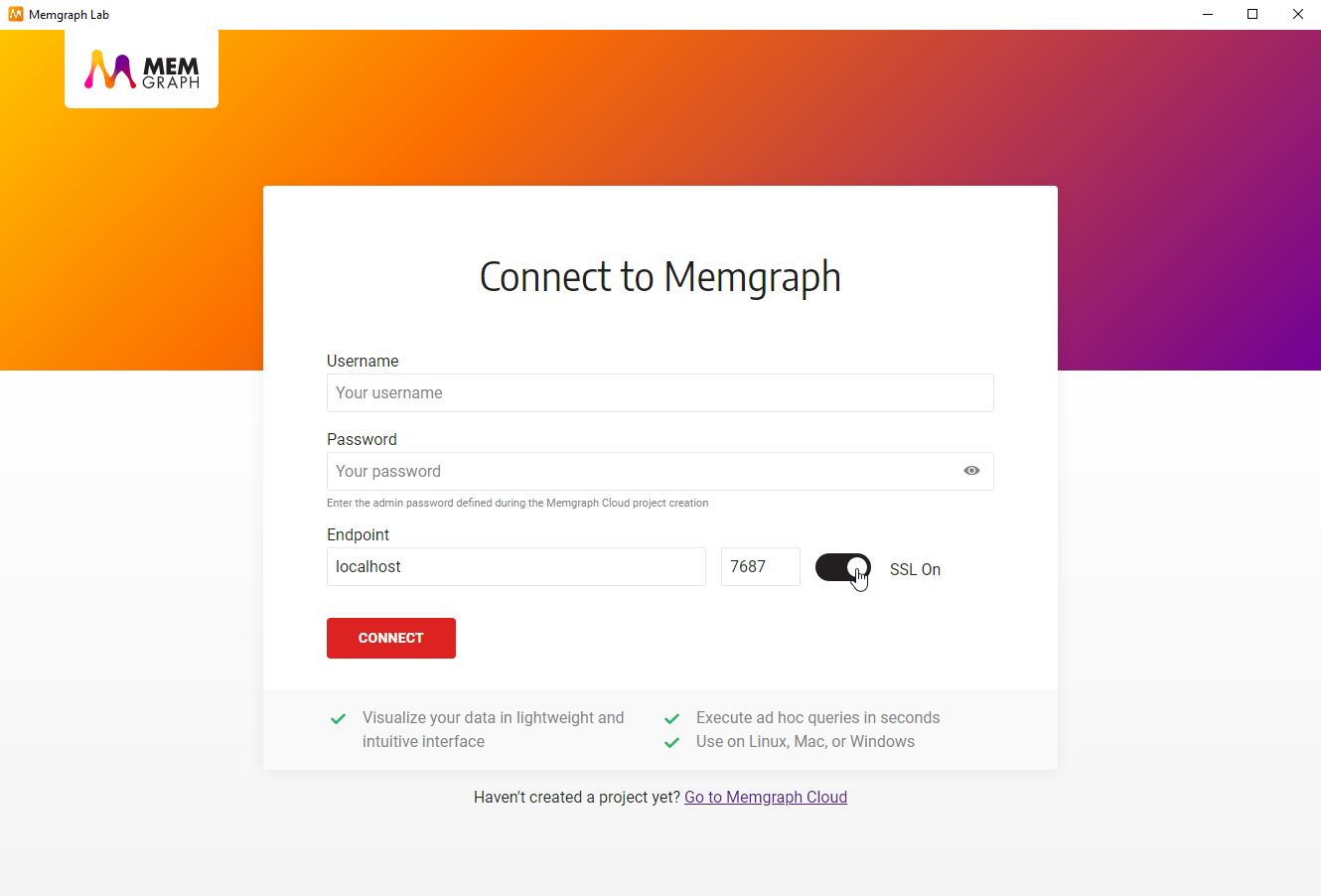
When Memgraph Lab is connected to MemgraphDB using SSL encryption, logs cannot be viewed inside the Lab.
When starting mgconsol include the --use-ssl=true flag. Flag can also be
explicitly set to false if needed.
When working with Memgraph Platform, you should pass configuration flags inside
of environmental variables as a part of the docker run command, for example:
docker run -it -p 7687:7687 -p 7444:7444 -p 3000:3000 -v mg_lib:/var/lib/memgraph -v mg_etc:/etc/memgraph -e MGCONSOLE="--use-ssl=true" memgraph/memgraph-platform
In all other cases passed them on as regular configuration flags.
For example, if you are starting mgconsole on Linux:
mgconsole --host 127.0.0.1 --port 7687 --use-ssl=true
or if you are using memgraph or memgraph-mage Docker images:
docker run -it -p 7687:7687 -p 7444:7444 -p 3000:3000 -v mg_lib:/var/lib/memgraph -v mg_etc:/etc/memgraph memgraph/memgraph-mage --use-ssl=true
Javascript
Use Neo4j driver for JavaScript, and
add +ssc to the UNI when defining a MEMGRAPH_URI constant:
MEMGRAPH_URI = 'bolt+ssc://18.196.53.118:7687'.Python
Use pymgclient, and add
sslmode=mgclient.MG_SSLMODE_REQUIRE to the mgclient.connect.
C/C++
Use mgclient, and add set the
params.use_ssl to true or false.
Go
Use the Neo4j driver for Go, and add +ssc
to the UNI: "bolt+ssc://18.196.53.118:7687".
PHP
Use the Bolt protocol library by stefanak-michal and add the following code
$conn->setSslContextOptions([
'passphrase' => 'bolt',
'allow_self_signed' => true,
'verify_peer' => false,
'verify_peer_name' => false
]);
C#
Use the Neo4j.Driver.Simple, and add
+ssc to the UNI: "bolt+ssc://18.196.53.118:7687".
Java
Use the Neo4j driver for Java and add
+ssc to the UNI: "bolt+ssc://18.196.53.118:7687".
Rust
Use mgclient, and add sslmode:
SSLMode::Require to the ConnectParams.
WebSocket over SSL is currently not supported in Memgraph.
